SailPoint Interview Questions And Answers
SailPoint Interview Questions And Answers For Beginners
1. What is SailPoint?
Ans. SailPoint is a software platform for identity management and governance. It helps organisations decide who can access what in their IT systems. It gives visibility into users, roles and entitlements, and helps automate access control policies. It supports both on-premises and cloud systems. The goal: reduce security risks and ease access management
2. What are the key features of SailPoint IdentityIQ?
Ans. IdentityIQ offers features like access certification, password management and policy enforcement. It automates user provisioning and de-provisioning, handles access requests, reporting and user lifecycle. It integrates with systems like Active Directory and gives admin dashboards. These help companies manage access efficiently and compliantly.
3. What is Identity and Access Management (IAM)?
Ans. IAM is about managing digital identities and controlling who can access which resources. It ensures only authorised people get access, and automates processes like account creation, role assignment or deactivation. It reduces manual errors and strengthens security. SailPoint is a tool that supports IAM.
4. What is Identity Governance?
Ans. Identity Governance is managing identities with security and compliance in mind. It involves defining who should have access, monitoring their activities, and reviewing access rights. SailPoint offers governance via access certifications, policy checks and reporting. This helps reduce unnecessary permissions and meet regulatory standards.
5. What is Identity Governance?
Ans. Identity Governance is managing identities with security and compliance in mind. It involves defining who should have access, monitoring their activities, and reviewing access rights. SailPoint offers governance via access certifications, policy checks and reporting. This helps reduce unnecessary permissions and meet regulatory standards.
6. What is SailPoint IdentityIQ used for?
Ans. IdentityIQ is used to manage user identities and control access across various IT systems. It handles onboarding, off-boarding and access changes automatically. It ensures compliance through certification campaigns and policies. It integrates with external systems and gives administrators visibility into access. Overall, it improves efficiency and security.
7. What is SailPoint IdentityIQ used for?
Ans. IdentityIQ is used to manage user identities and control access across various IT systems. It handles onboarding, off-boarding and access changes automatically. It ensures compliance through certification campaigns and policies. It integrates with external systems and gives administrators visibility into access. Overall, it improves efficiency and security.
8. What is SailPoint IdentityIQ used for?
Ans. IdentityIQ is used to manage user identities and control access across various IT systems. It handles onboarding, off-boarding and access changes automatically. It ensures compliance through certification campaigns and policies. It integrates with external systems and gives administrators visibility into access. Overall, it improves efficiency and security.
9. What is an Identity Cube in SailPoint?
Ans. An Identity Cube is a data model representing one user’s digital identity in SailPoint. It holds information like the user’s name, roles, accounts and entitlements across all connected systems. This gives admins a complete view of a user’s access. Identity Cubes update automatically during aggregation and are central to governance.
10 . What are entitlements in SailPoint?
Ans. Entitlements are specific permissions or access rights granted to a user (for example: “can create invoices”). They define what actions a user can perform in a system. SailPoint collects entitlement data during aggregation and may group them into roles. Good entitlement management ensures “least-privilege” and lowers security risk.
11. What is a connector in SailPoint?
Ans. A connector is a link between SailPoint and an external system/application (for example: Active Directory, SAP). It enables SailPoint to fetch user data (aggregation) and to apply changes (provisioning/de-provisioning). Connectors simplify integration and automation. Without them, much of the work would be manual.
12. What is provisioning in SailPoint?
Ans. Provisioning is the process where SailPoint automatically creates or updates user accounts in target systems. For example, when a new employee joins, the system gives them access; when they leave, access is removed. This reduces manual workload, speeds up access and ensures security.
13. What is aggregation in SailPoint?
Ans. Aggregation means collecting data (user accounts, roles, entitlements) from connected systems into SailPoint. It builds a complete identity view by fetching information from all resources. The collected data populates Identity Cubes and helps in reporting and certification.
14. What is de-provisioning?
Ans. De-provisioning is removing user access when it’s no longer needed—like when someone leaves or moves roles. SailPoint automates this to prevent orphaned accounts or unwanted access. It helps maintain security and compliance by ensuring only valid users retain access.
15. What is a user lifecycle in SailPoint?
Ans. A user lifecycle refers to the stages of a user’s time in an organisation: onboarding, role changes/promotions, transfers, off-boarding. SailPoint automates access control in each stage via workflows and policies. This ensures users have appropriate access all throughout their employment.
16. What are the different components of SailPoint?
Ans. SailPoint comprises components such as IdentityIQ (core app), connectors (to external systems), workflows (automated sequences), rules (custom logic), reports and dashboards. These work together to streamline identity management, governance and compliance.
17. What is the role of policies in SailPoint?
Ans. Policies define rules and security guidelines about who should or should not have access. For example, a policy may block simultaneous “maker” and “checker” roles. SailPoint uses policies to trigger alerts, detect violations and enforce access constraints.
18. What is a rule in SailPoint?
Ans. A rule is a small piece of code (often using BeanShell) which allows custom logic within SailPoint processes (aggregation, provisioning, certification). Rules help tailor the system to business needs, implement checks or transformations during runtime.
19. What is a role in SailPoint?
Ans. A role is a collection of access rights/entitlements grouped by job function (e.g., “HR Manager”). Assigning a role to a user gives them all the rights that go with it. This simplifies access management, supports least privilege and improves consistency.
20. What is role-based access control (RBAC)?
Ans. RBAC is a method where users get access based on their role rather than individual permissions. For example, all HR staff get the “HR Role” rather than each user getting rights individually. SailPoint supports RBAC by letting admins define roles and assign them automatically.
21. What is role mining?
Ans. Role mining is the process of discovering roles by analysing existing user permissions and usage patterns. SailPoint analyses accounts to find common entitlement combinations, then suggests roles. This helps organisations build cleaner, efficient access profiles.
22. What is certification in SailPoint?
Ans. Certification is reviewing and verifying whether users still need their access rights. SailPoint uses campaigns where managers/auditors approve, reject or delegate access. This process keeps access current and compliant.
23. What is certification in SailPoint?
Ans. Compliance management ensures that identity and access processes align with company rules and regulations (e.g., GDPR, SOX). SailPoint automates reviews, policy enforcement and reporting, helping organisations avoid penalties and security incidents.
24. What is a provisioning policy?
Ans. A provisioning policy defines the rules for creating/modifying user accounts (e.g., naming conventions, required attributes). It ensures standardisation, accuracy and compliance during provisioning tasks.
25. What are access requests in SailPoint?
Ans. Access requests let users ask for extra permissions via a self-service portal. Instead of emailing IT, users make requests which go through approval workflows. Once approved, SailPoint provisions the access. This speeds up access and reduces manual work.
26. What is a workflow in SailPoint?
Ans. A workflow is an automated sequence of steps (for example: request → approve → provision → notify). In SailPoint it handles processes like access requests, certifications and provisioning. Workflows save time and standardise how tasks are done.
27. What is the difference between manual and automated provisioning?
Ans. Manual provisioning means an IT person must create or update accounts by hand—slow and error-prone. Automated provisioning means SailPoint handles this automatically based on rules/policies—faster, more accurate and compliant.
28. What are the main modules in SailPoint IdentityIQ?
Ans. Key modules include Compliance Manager (handles certifications/policies), Lifecycle Manager (handles access requests/provisioning), Identity Intelligence (for reporting/analytics), and the Governance Platform (ties them together). They each serve distinct purposes for identity governance.
29. What is a policy violation?
Ans. A policy violation occurs when a user’s access breaks a defined rule (for example: giving both “approve” and “pay” rights to the same person). SailPoint detects such violations automatically and triggers alerts for review or remediation.
30. What scripting language is used in SailPoint?
Ans. SailPoint uses BeanShell, which is a Java-based scripting language. It allows admins/developers to write custom logic inside rules and workflows. Knowing basic Java helps in writing these scripts.
31. What scripting language is used in SailPoint?
Ans. SailPoint uses BeanShell, which is a Java-based scripting language. It allows admins/developers to write custom logic inside rules and workflows. Knowing basic Java helps in writing these scripts.
32.What is a managed resource in SailPoint?
Ans. A managed resource is any external system or application that SailPoint connects to (such as Active Directory, SAP, database). SailPoint uses connectors to manage accounts, entitlements and passwords in these resources.
33.What are lifecycle events in SailPoint?
Ans. Lifecycle events are triggers such as hiring, promotion, department transfer or termination of employees. SailPoint uses these events to initiate workflows that adjust user access accordingly—onboarding, role changes or off-boarding.
34. What is the difference between the 4 pillars of IAM?
Ans. The four IAM pillars are Authentication (verify who you are), Authorization (what you can access), Administration (managing identities/roles) and Audit & Compliance (tracking activity and ensuring rules are followed). SailPoint supports all of these to maintain secure identity operations.
35. What are the 4 I’s of SailPoint?
Ans. The 4 I’s stand for Identity (who has access), Intelligence (why they have it), Integration (how systems are linked) and Insight (what risks exist and how to fix them). These guide how SailPoint delivers identity governance and access control.
36. What is the difference between IdentityNow and SailPoint Identity Security Cloud?
Ans. IdentityNow is SailPoint’s earlier cloud-based identity governance solution for mid-sized organisations. The Identity Security Cloud is a next-gen unified cloud platform designed for larger enterprises, with AI/ML for deeper analytics and automation. So, IdentityNow = simpler SaaS; Identity Security Cloud = advanced enterprise solution.
37. How does SailPoint support Zero Trust security architecture?
Ans. SailPoint follows “never trust, always verify”—so even trusted users’ access is checked continuously. It monitors behavioural anomalies, removes unnecessary access, integrates with MFA/PAM tools, and uses analytics for risk-based decisions. This helps reduce insider threats and increases security.
38. What are the main components of SailPoint Identity Security Cloud?
Ans. The Identity Security Cloud includes modules like Access Modeling (what access exists), Access Requests, Certifications, Provisioning, and Identity Intelligence (analytics/AI). It connects cloud and on-prem apps via APIs and provides real-time risk visibility and automation.
39. What is Access Certification in SailPoint and why is it important?
Ans. Access Certification is regularly reviewing user access to confirm it’s still valid and needed. With SailPoint admins can run campaigns where managers/auditors approve or revoke access. It ensures users don’t keep unnecessary rights, reduces risk, and supports regulatory compliance.
40. How does SailPoint integrate with Active Directory and Azure Active Directory?
Ans. SailPoint uses pre-built connectors to link with AD and Azure AD to manage user accounts, groups and access rights. It synchronises identity data between those systems and SailPoint, supports hybrid environments and enforces policies across both on-prem and cloud directories.
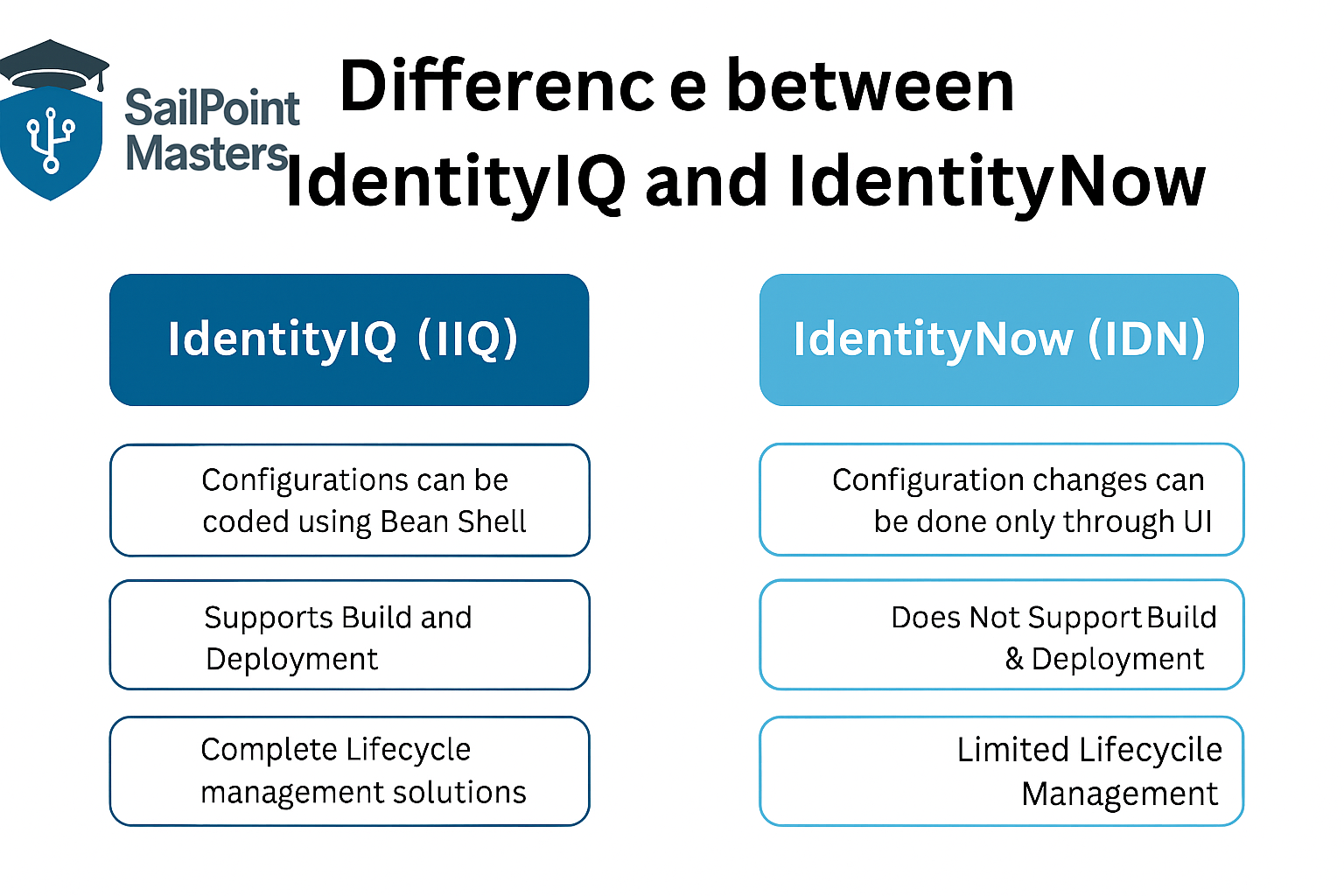
41. What is the difference between IdentityIQ and IdentityNow?
Ans. IdentityIQ is the on-premises solution of SailPoint—deeply customisable, rule-based, for complex enterprise scenarios. IdentityNow is the cloud-based SaaS solution—faster to deploy, easier to maintain, intended for simpler/hybrid setups. Choice depends on organisation’s needs.
42. How does SailPoint handle role-based access control (RBAC)?
Ans. SailPoint allows defining business, IT and composite roles that group entitlements by job function. Assigning a role to users gives them the bundled permissions automatically. It supports role mining to discover roles from existing data and enforces least privilege and standardised access.
43. What is SoD (Segregation of Duties), and how is it implemented in SailPoint?
Ans. SoD ensures one person doesn’t hold conflicting permissions (e.g., approving and paying invoices). SailPoint enforces SoD via policies, detects violations and alerts appropriate people. It automates reviews and prevents fraud by enforcing internal controls and compliance.
44. What is an Aggregation Task in SailPoint?
Ans. An Aggregation Task is a scheduled job that collects identity data (users, accounts, entitlements) from connected systems into SailPoint. This builds a full view of who has what access, populates Identity Cubes, and supports reporting/governance efforts.
45. How does SailPoint detect and prevent orphaned accounts?
Ans. Orphaned accounts are user accounts with no valid owner (e.g., former employee). SailPoint detects these during aggregation and correlation by checking identity records against application accounts. It flags and removes them, reducing unauthorized access risk and maintaining clean systems.
46. What is a correlation rule, and how does it work in IdentityIQ?
Ans. A correlation rule defines how SailPoint links accounts from various systems to a single identity. It uses match logic like email address, employee ID or username. If no identity matches, it can create a new one. This ensures accurate identity representation and prevents duplicates.
47. What are the different types of connectors available in SailPoint?
Ans. Connectors in SailPoint include out-of-the-box types (AD, SAP, database), generic ones (JDBC, REST, LDAP) and custom connectors (for unique systems built using Java/BeanShell). They handle aggregation, provisioning and password management. Good connector setup is vital for smooth identity operations.
48. How does SailPoint ensure compliance with regulations like GDPR or SOX?
Ans. SailPoint automates access reviews, certifications, and policy enforcement, gives full visibility of who has access to what data. It logs and reports all activities, supports SoD controls and ensures timely removal of access when no longer needed. This helps organisations meet regulatory obligations.
49. What is the purpose of the Identity Cube in SailPoint?
Ans. The Identity Cube holds a full profile of a user—accounts, entitlements, roles, risk scores across all systems. SailPoint uses this as the “single source of truth” to analyse, manage and audit identities. It updates automatically and supports governance decisions.
50. What is an entitlement in SailPoint?
Ans. An entitlement is a specific permission or right in an application (for example: “read access to payroll”). SailPoint tracks, assigns and revokes entitlements during aggregation, provisioning and certification. Proper entitlement management prevents users from getting excessive rights and strengthens security.
- Want to learn more about our SailPoint Certification Training In Hyderabad
51. What is an entitlement in SailPoint?
Ans. Provisioning methods include automated (rules/workflows) and manual (IT does it by hand or via approval). It may be real-time, delayed or batch. SailPoint uses policies/rules to define how provisioning happens. Automation ensures speed, accuracy and compliance.
52. How do you manage access for users moving between departments?
Ans. When a user transfers departments, SailPoint uses lifecycle events, workflows and policies to change their access accordingly. Old roles/entitlements get revoked, new ones assigned automatically. This ensures the user has correct access at all times and avoids risk of retained unnecessary permissions.
53. What is the difference between direct, indirect and inherited entitlements?
Ans.
- Direct entitlements: assigned to the user individually.
- Indirect: granted via a role or policy.
- Inherited: gained from a parent role/group structure.
SailPoint tracks all of these to give accurate visibility and simplify certifications and risk analysis.
SailPoint Interview Questions And Answers For Experienced
54. What is the difference between rules and policies in SailPoint?
Ans. Rules are custom logic (code) that automate behaviour (for example: modify a username or enforce attribute logic). Policies are governance standards that define permissible access and detect violations. Rules execute actions; policies govern constraints. Together they allow flexibility + control in SailPoint.
55. How does SailPoint integrate with ServiceNow?
Ans. SailPoint integrates with ServiceNow so users can submit access requests via ServiceNow’s self-service portal. SailPoint workflows then process these requests automatically. It also synchronises user data between both systems. Integration reduces manual ticketing and improves user experience and compliance.
56. What are triggers in IdentityNow?
Ans. In IdentityNow, triggers are events (such as “new user created”) that start automated actions like provisioning workflows. They may use webhooks or API calls to react in real time. Triggers enable event-driven automation without manual intervention.
57. What is the IdentityIQ Plugin Framework?
Ans. The Plugin Framework allows developers to extend SailPoint’s capability without modifying core code. Developers write plugins (in Java) that add new features (dashboards, forms, integrations). Plugins run in isolation for stability. This approach keeps the system upgrade-friendly and customisable.
58. What is the difference between incremental and full aggregation?
Ans.Full aggregation: pulls all data from connected systems; ensures complete accuracy but takes longer.
Incremental aggregation: pulls only changed or new data since last run; faster and more efficient for frequent updates.
Both are needed: full for baseline, incremental for ongoing sync.
59. What is the difference between incremental and full aggregation?
Ans. Reconciliation checks that what SailPoint believes to be the state of accounts/entitlements matches what exists in target systems. Any mismatch triggers correction or alert. This ensures data integrity across systems and supports audit readiness.
pulls only changed or new data since last run; faster and more efficient for frequent updates.
Both are needed: full for baseline, incremental for ongoing sync.
60. What are the types of certifications in SailPoint?
Ans. Certifications can be: Manager-certifications (review access for direct reports), Role-certifications (review entitlements inside roles), Application certifications (review system-specific access), Account-group certifications (review shared/privileged accounts). Each type handles a different governance angle.
61. What is a Compliance Manager in SailPoint?
Ans. Compliance Manager is the module that oversees certifications, policy enforcement and SoD checks. It gives dashboards, reports and supports audit-tracking. It helps organisations meet regulatory requirements by automating governance and monitoring.
62. What is an entitlement catalog?
Ans. An entitlement catalog is a central list of all entitlements across connected systems. It provides visibility into what access rights exist and are available for request. With it, administrators can classify, search, assign entitlements and support certification and governance.
63. What are security best-practices for SailPoint?
Ans. Some best practices: enforce least-privilege access, run regular certifications and SoD checks, keep connectors and the SailPoint system up-to-date, encrypt sensitive data and secure communication, audit and log provisioning activities, avoid hard-coded credentials in scripts, implement multi-factor authentication for critical access, monitor continuously.
64. How do you migrate configurations between environments?
Ans. Migration involves exporting configurations (rules, workflows, forms) from one environment (e.g., dev) and importing into another (e.g., prod). SailPoint offers import/export utilities and uses XML files for config. It’s best to test in a staging environment, track versions and document changes to avoid deployment issues.
65. What are custom tasks in SailPoint?
Ans. Custom tasks are user-defined jobs (written via scripts) that automate organisation-specific operations (data cleanup, special reports) beyond out-of-the-box functions. They are defined in Task Definitions, scheduled or run manually. They add flexibility to suit unique business needs.
66. What are pre-deployment checks for SailPoint implementation?
Ans. Before going live you should: verify server resources, database connectivity and network configurations; test all connectors with credentials; review policies, rules and workflows for errors; ensure backups are available; run pilot tests with sample data; ensure documentation is in place and stakeholders trained. This reduces risk.
67. How do you upgrade SailPoint IdentityIQ?
Ans. Upgrading requires backup of configurations, databases and customisations, installing the new version, merging configuration files carefully. Review release notes to identify deprecated features. Test workflows/connectors/rules in a staging environment. Once validated, deploy in production. Upgrading ensures better performance and security.
68. What are common challenges faced during SailPoint deployment and how to handle them?
Ans. Common challenges: data inconsistency, connector failures, mis-configured rules, poor user adoption. Handling them requires detailed planning and testing, using staging environments, accurate data mapping, monitoring logs for early errors, providing admin/user training, and documenting/translating lessons learned for continuous improvement.
69. What problem does SailPoint solve?
Ans. SailPoint solves the challenge of controlling and securing user access across many systems in an organisation. As businesses grow, managing who accesses what becomes complex and risky. SailPoint automates and governs the full access lifecycle, helping reduce unauthorised access, data breaches and compliance violations.
70. Who are SailPoint’s top competitors?
Ans. SailPoint’s main competitors in the IAM/IGA space include Okta, CyberArk, Ping Identity and Oracle Identity Manager. Each offers identity and access solutions. SailPoint stands out for deep identity governance, lifecycle management and compliance.
71.What language is used in SailPoint?
Ans. SailPoint uses BeanShell (a lightweight Java-based scripting language) for custom logic in rules and workflows. It also uses XML files for workflows, configuration and forms. Knowledge of Java and XML helps in customizing SailPoint to fit business requirements.
72.What are the types of entitlement assignment: direct, indirect and inherited?
Ans.
- Direct: the user is assigned the entitlement individually.
- Indirect: the user gets it via a role or policy assignment.
- Inherited: the entitlement comes through a parent role/group structure (e.g., role A inherits from role B).
SailPoint tracks all of them to understand the complete access picture.
customizing SailPoint to fit business requirements.
73. What is identity attestation?
Ans. Identity attestation is the process of verifying if a user’s access and attributes are correct and still needed. Managers/auditors review identities through SailPoint interface, confirming or revoking access. It supports audit readiness and helps prevent privilege creep or misuse.
74. What is identity attestation?
Ans. Identity attestation is the process of verifying if a user’s access and attributes are correct and still needed. Managers/auditors review identities through SailPoint interface, confirming or revoking access. It supports audit readiness and helps prevent privilege creep or misuse.
75. How do you troubleshoot provisioning errors in SailPoint?
Ans. To handle provisioning failures: review task results and logs, verify target system connectivity/permissions, check provisioning policies and mandatory attribute mappings, identify errors in BeanShell scripts, test provisioning manually if needed. Continuous monitoring helps keep errors under control.
76. How do you troubleshoot provisioning errors in SailPoint?
Ans. A provisioning interceptor is a rule that lets you insert custom logic during provisioning—like checking if a username already exists or applying a naming convention. It runs automatically when a provisioning plan executes. It enhances flexibility and ensures policy compliance.
77. What is identity correlation logic?
Ans. Correlation logic links user accounts from different systems to one identity in SailPoint by comparing attributes (email, employee ID, username). Good correlation ensures you have one unified view of each user across systems. This prevents duplicate identities and orphan accounts and keeps access data clean.
78. What is a managed attribute refresh task?
Ans. This task updates managed attributes (like department, title) in SailPoint so that role assignments and policies remain accurate. When a user’s details change, the refresh task updates them automatically, ensuring access stays aligned with current status. It helps maintain governance integrity.
79. What are the steps for creating a certification campaign?
Ans. Steps include: choose campaign type (manager, role, application), select users/systems to review, set reviewers, define start/end dates, set escalations/reminders, launch the campaign. SailPoint then sends tasks, records responses and applies changes. Reports show completion status and help the organisation stay compliant.
80.What is manager certification?
Ans. Manager certification is where managers review access of their direct reports. They get a list of what each report has access to and can approve or revoke it. Helps ensure team members only have what they need. It’s a critical governance step for access reviews.
81. What is role-composition certification?
Ans. Role-composition certification reviews the entitlements inside roles to check whether each right is still valid. Reviewers assess the access bundled in the role to prevent the role from accumulating unnecessary or risky permissions. This keeps roles clean and meaningful.
82. What is the difference between application onboarding and identity onboarding?
Ans. Application onboarding means integrating a new system into SailPoint—including connector setup, schema mapping and provisioning rules. Identity onboarding means importing new user data (such as new employees) into SailPoint. Both are required for full identity lifecycle coverage.
83. How does SailPoint manage privileged access?
Ans. SailPoint integrates with PAM tools (like CyberArk) to manage privileged accounts (e.g., admin accounts). It enforces strict policies, tracks privileged activity, requires approvals/time-limits access and monitors usage. This ensures high‐risk accounts are governed securely.
84. What are IdentityIQ tasks and task definitions?
Ans. Tasks are jobs that perform actions (e.g., aggregation, certification generation). Task definitions describe how the task runs, what it does, when it triggers, and what notifications it sends. SailPoint lets administrators customise tasks through XML. They’re core to automation.
85. How do workflows differ between IdentityIQ and IdentityNow?
Ans. In IdentityIQ (on-premises), workflows are defined via XML and BeanShell scripting and allow deep customisation. In IdentityNow (cloud/SaaS), workflows are simpler, often drag-and-drop or UI-based, with less coding required. Both handle requests/approvals/provisioning but differ in flexibility and deployment style.
86. What is role mining and why is it relevant in large organisations?
Ans. Role mining analyses existing user access to find patterns and suggest meaningful roles. In large organisations with many users and complex entitlements, this helps simplify access assignments, reduce redundancy and enforce least privilege more effectively.
87. What is policy violation remediation in SailPoint?
Ans. Remediation is the process of resolving a policy violation detected by SailPoint—for example, identifying someone with conflicting roles, revoking or modifying access, notifying managers and logging the action. Automation of remediation improves governance and reduces risk.
88. What are static vs dynamic roles?
Ans.
- Static roles: manually assigned and fixed until an administrator changes them.
- Dynamic roles: automatically assigned/unassigned based on criteria (like department or job title) evaluated in real-time.
Dynamic roles improve agility and reduce administrative overhead.
89. What are static vs dynamic roles?
Ans.
- Static roles: manually assigned and fixed until an administrator changes them.
- Dynamic roles: automatically assigned/unassigned based on criteria (like department or job title) evaluated in real-time.
Dynamic roles improve agility and reduce administrative overhead.
90. How does SailPoint support multi-application provisioning?
Ans. SailPoint uses connectors and workflows so that when a user is created, they automatically get accounts/access across multiple applications. Policies determine what access they need per system, and logs capture any failures. This maintains consistency across a large ecosystem.
91. What is the workflow engine in SailPoint?
Ans. The workflow engine is the component that executes business processes (approvals, provisioning, certification) defined in XML along with rules and conditions. It supports branching, error handling, rollback, notifications and triggers from events. It makes identity-process automation possible.
92. What are the main files used in workflow configuration?
Ans. Workflow configuration files in SailPoint include XML definition files (workflow definitions), approval step files, task-rule files and custom scripts. These describe how each workflow runs, its steps and logic. They’re imported via the admin console and must be tested for correct behaviour.
93. How do you configure a connector in SailPoint?
Ans.To configure a connector: specify connection details (hostname, credentials, etc.), choose connector type (AD, SAP, DB), map schema (which attributes or accounts to pull), test the connection for validity. Then set rules/custom logic if needed. Once configured, aggregation and provisioning can work smoothly.
94. How do you handle custom connectors in SailPoint?
Ans. If a target system isn’t supported out-of-the-box, you build a custom connector using Java or BeanShell. You define how the system communicates with SailPoint (aggregation/provisioning). After development, the custom connector can be deployed and reused across environments.
95. What is identity correlation logic and why is it important?
Ans. Correlation logic matches user accounts from different systems to a single identity in SailPoint by checking attributes (like email or employee ID). Without accurate correlation you risk duplicates, orphan accounts or mis-assigned permissions. It is crucial for clean identity governance.
96. What are the main challenges in SailPoint deployment and how to mitigate them?
Ans. Main challenges include inconsistent data, connector failures, complex customisations, user adoption issues. To mitigate: plan carefully, use staging environments, perform thorough testing, validate data mappings, monitor logs early, train stakeholders and document everything.
97. What is the difference between application vs identity onboarding from a certification viewpoint?
Ans. Application onboarding adds a new system to governance scope (new connector and schema). Identity onboarding adds user identities (new employees/contractors) to the system. When certifying, you may need to review either the application’s access (application onboarding) or a new set of identities (identity onboarding).
98. What is the purpose of a managed attribute refresh task?
Ans. This task keeps user attribute data (department, job title) up to date in SailPoint. When a user’s department changes, the refresh updates the attribute so that roles/policies trigger correctly. It sustains accurate access control and ensures governance decisions are based on current information.
99. How do you handle failed provisioning or aggregation tasks?
Ans. When a task fails: review logs for errors, check connector settings, credentials, network access, check policies/rules for missing attributes or logic errors, test manually if needed, correct the issue and re-run in debug mode. Document the cause to avoid future failures.
100. How do reporting and analytics features in SailPoint support governance?
Ans. SailPoint offers dashboards, risk reports and access summaries. They show users with high-risk entitlements, policy violations, access trends. Admins and auditors can use these insights to make decisions and plan remediation. Strong reporting supports compliance and helps improve identity risk posture.